 News
News HONG KONG - Jie Yu recently delivered a talk on security technologies that enable compliance at the "Web 3.0 HK Security and Compliance Core Technology Framework Symposium." This event was spearheaded by the Hong Kong Web3 Association and co-hosted with the Web3 Infrastructure Foundation.
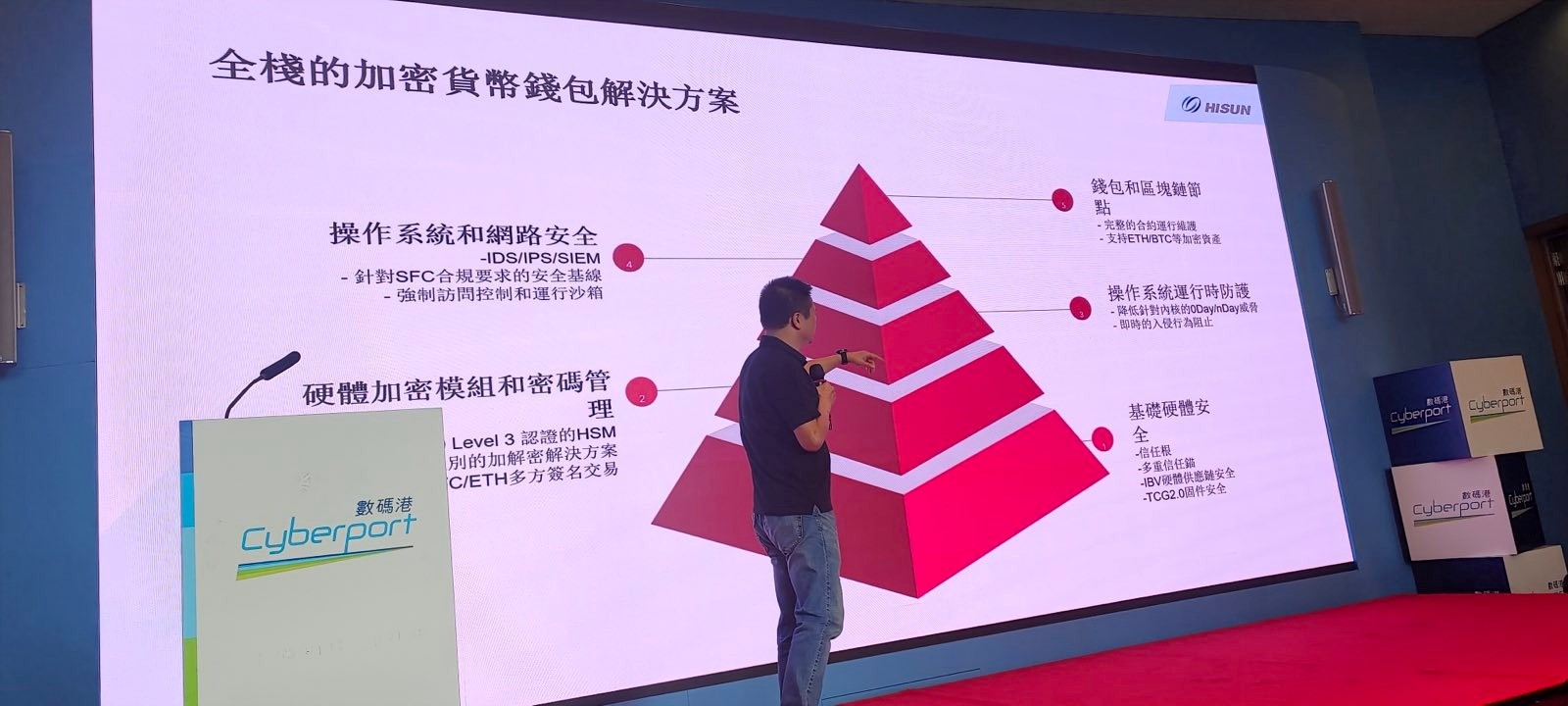
The symposium aimed to guide Web 3.0 enterprises through the new licensing mandates introduced by the Securities and Futures Commission (SFC) of Hong Kong earlier this year. The SFC directives set rigorous security and operational benchmarks for aspiring virtual asset service providers (VASPs) and virtual asset trading platforms (VATPs).
Key stipulations set by the SFC encompass:
Cold Wallet Asset Storage - A minimum of 98% of user assets should be safeguarded in cold wallets. This implies that the private keys are retained offline, shielded from regular access by internet-connected hot wallets, fortifying them against potential cyber-attacks and theft.
HSM-Based Key Management - Prospective entities must employ certified hardware security modules (HSMs) for private key management, diverging from the more conventional multi-party computation (MPC) methods that present more vulnerabilities. HSMs offer tamper-proof hardware encryption.
Third-Party Audits - Proposed solutions must undergo independent security evaluations by accredited experts before implementation and at regular intervals post-deployment. This ensures an external endorsement of their security protocols.
Yu's discourse unveiled a comprehensive crypto wallet system architecture that aligns seamlessly with the SFC's advisories on security, governance, and operational controls prerequisite for licensing.
Industry stakeholders have hailed these advancements, interpreting them as indicative of the regulatory sophistication essential for the sustainable growth of Web 3.0.
In another enlightening presentation, Shawn Chang, the co-founder of W3IF and founder of HardenedVault, delved into the trinity of cypherpunk security, enterprise security, and regulation/compliance. He outlined the interrelation of these three elements in the evolving digital landscape.

Historically, three manifestos have significantly influenced the world we inhabit:
* The GNU Manifesto (1983) sparked the free software movement, advocating for transparency through open source.
* A Hacker's Manifesto (1986) offered a unique perspective on the world, encouraging individuals to embrace their curiosity and venture into new fields.
* The Cypherpunk Manifesto (1993) emphasized the cruciality of privacy, deniability, and anonymity in modern society, urging us to strive for these values.
These manifestos highlight the ideal world we, as humans, should strive for. However, reality often falls short. A Phrack paper, "Smash the Stack for Fun and Profit," describes how to exploit memory corruption vulnerabilities, effectively setting the stage for cyber warfare. Despite nearly three decades of battling memory war, we have frequently found ourselves on the losing side even though robust defenses like PaX/GRsecurity and isolation mechanisms (like Qubes OS) exist in some technical fields. However, new problems continue to emerge, often quietly and rapidly.
Old-school hackers will recall the 2007 Phrack paper, "Attacking the Core," which targeted Ring 0 (Kernel space). However, the kernel is no longer the "Core". We now have a complex system of Turing machines running on other Turing machines. Simply put, you buy multiple machines when you purchase a laptop, desktop PC, or server. You're also acquiring hidden machines like Intel CSME, AMD PSP, and BMC that could be exploited maliciously.
Unfortunately, these issues can't be resolved solely through enterprise security solutions driven by compliance and regulation. Solutions like EDR, HIDS, XDR, SIEM, and zero trust have been marketed well, but they can be compromised by a few hours of work by a savvy security researcher. What do you expect if organized crime or state-actors are in your threat model? Even the fanciest, AI-driven enterprise solutions for analyzing suspicious logs can be rendered useless if an attacker compromises the agent or server first and alters the data.
Shawn highlighted the importance of transparency and self-sovereignty, referencing the NSA's supply chain hijacking exposed by Snowden. Cypherpunks are left questioning how to trust vendors when even massive surveillance agencies can't be trusted. Open source doesn't guarantee security but provides transparency, allowing for proper auditing. This issue is particularly relevant when an organization runs a custody operation, potentially in a random >= Tier-3 data center. Many may believe that an HSM with a certification is sufficient, which might be the case on an enterprise security level (with exceptions like hedge funds). However, for cypherpunk security, this is merely the starting point. A genuinely secure solution would allow users to provision the hardware, firmware, and OS following best practices. You should only trust a key you own, not one managed by a corporation in another country. This challenges regulated cryptocurrencies as most regulators need to understand infrastructure security.
Shawn also addressed Web3 infrastructure, noting that there are three approaches to achieving decentralization, with blockchain being just one of them. We shouldn't ignore relay (Nostr/Tor) and federation (XMPP/Matrix, etc.).
In conclusion, Shawn emphasized that Hong Kong and the world desperately need open-source solutions that users can audit if they wish rather than blindly trusting a closed-source vendor. We can create a solid foundation for cybersecurity by reducing the likelihood of backdoors. This will be challenging, but it's the only way forward. Welcome to the desert of the real!
Eli Ma, an individual member of the governing board of Web3 Infrastructure Foundation, introduced the innovative "Mega" project, a fresh perspective on Git refactoring with the vision of promoting anonymous and decentralized open source in the Web 3.0 landscape.
The presentation, titled "Git Refactoring - Paving the Way for Anonymous, Decentralized Open Source in the Web 3.0", delved into the intricacies and advancements in version control and code management for a decentralized web setting.

Web 3.0: The Next Frontier Web 3.0, while still a fluid concept, is often associated with data sovereignty, decentralization, and anonymity. Yet, the roadmap for managing code within this paradigm still needs to be defined. Mega bridges this gap with unique designs and implementations that deviate from conventional Git services.
1. Data Sovereignty: At the heart of Mega's ethos is that every developer or organization should retain complete ownership of their code. While platforms like GitHub and GitLab are primary hosts for numerous code repositories, they might occasionally modify code access in response to specific regulatory guidelines. Drawing inspiration from Google Piper's paper, Mega is tailored for corporate and individual developers, ensuring unyielding control over source code assets.
2. Decentralization: Git inherently offers a decentralized version control mechanism. However, the ascent of platforms like GitHub has centralized the open-source collaboration process. Mega's ambition is to decentralize the sharing and collaborative aspects of coding. By leveraging Distributed Hash Table (DHT) and bespoke Git transfer protocols, Mega enables seamless interactions between nodes, encompassing pull, push, and clone functionalities.
3. Anonymity: Still in its nascent phase, Mega envisions adopting Nostr's anonymous identity blueprint, anchoring Public Keys as the cornerstone of its authorization system. This approach ensures that future open-source collaborations and sharing will be independent of centralized entities and untraceable developers, echoing the mantra of "Paving the Way for Anonymous, Decentralized Open Source in the Web 3.0".
Under the aegis of the Web3 Infrastructure Foundation, Mega is poised to be an indispensable asset for Web 3.0 developers. Its vision transcends traditional economic models, aiming to make a tangible impact in the resurgence and growth of the Cypherpunk movement within the Web 3.0 realm.
The final session of the conference hosted an insightful panel discussion on the various dimensions of Hong Kong's newly issued regulation on virtual assets by the Securities and Futures Commission (SFC). The panelists, with their diverse backgrounds in business, law, and technology, shared their unique perspectives on this new regulatory landscape for virtual assets.

For an in-depth look at the presentation and insights into the decentralized open source's future trajectory, visit here.